October Microsoft Patch Tuesday Commentary from Ivanti
- Written by Todd Schell, Senior Product Manager, Security, Ivanti
October Patch Tuesday Commentary
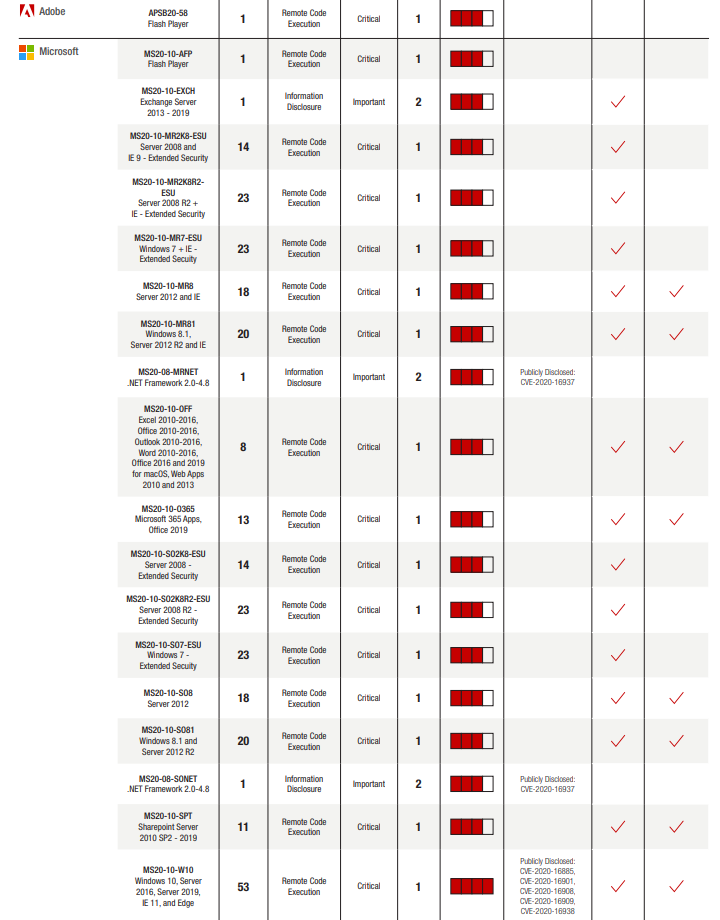
Microsoft has decided to break the 100 CVEs per month streak. Currently there are only 87 distinct CVEs being resolved in the October Patch Tuesday release. Six of these CVEs have been Publicly Disclosed, which means threat actors have had a jump start on being able to research and engineer exploits. It will be a good idea to treat those as a higher risk this month to be safe.
Microsoft has launched the preview of their new update guide. It has provided a few nice improvements. Quick access to more of the risk-focused information can be found in the vulnerabilities view. Columns like Exploited and Publicly Disclosed allow you to sort and view quickly to see if there are high risk items. Like our six CVEs this month that are publicly disclosed. Public Disclosure could mean a couple things. It could be that a demonstration of exploit was performed at an event or by a researcher. It could also mean proof-of-concept code has been made available. In any case a public disclosure does mean that threat actors have advanced warning of a vulnerability and this gives them an advantage. The mean time to exploit a vulnerability is 22 days according to a research study from the RAND Institute. If a threat actor gets advanced notice of a vulnerability, they could have a head start of days or even weeks, meaning an exploit may not be very far off. This is one risk indicator that can help companies prioritize what to act on first from a threat perspective.
This month five of the publicly disclosed updates affect Windows 10 and corresponding server editions (CVE-2020-16908, CVE-2020-16909, CVE-2020-16901, CVE-2020-16885, CVE-2020-16938). The sixth affects .Net Framework CVE-2020-16937.
One interesting things this month— there are no browser vulnerabilities being resolved. At the time of release Microsoft did not have any CVEs reported against IE or Edge and no listing of the browsers as affected products this month. Not sure I remember the last time that has happened.
A couple of CVEs of note this month:
CVE-2020-16947 is a vulnerability in Microsoft Outlook which could allow Remote Code Execution. Affected versions of Outlook can be exploited just by viewing a specially crafted email. The Preview Pane is an attack vector here, so you don’t even need to open the mail to be impacted. The flaw exists within the parsing of HTML content in an email. Patch this one quickly. It will be an attractive target for threat actors.
CVE-2020-16891 is a vulnerability in Windows Hyper-V which could allow Remote Code Execution. This patch corrects a bug that allows an attacker to run a specially crafted program on an affected guest OS to execute arbitrary code on the host OS. A guest OS escape like this would also be very attractive to threat actors.